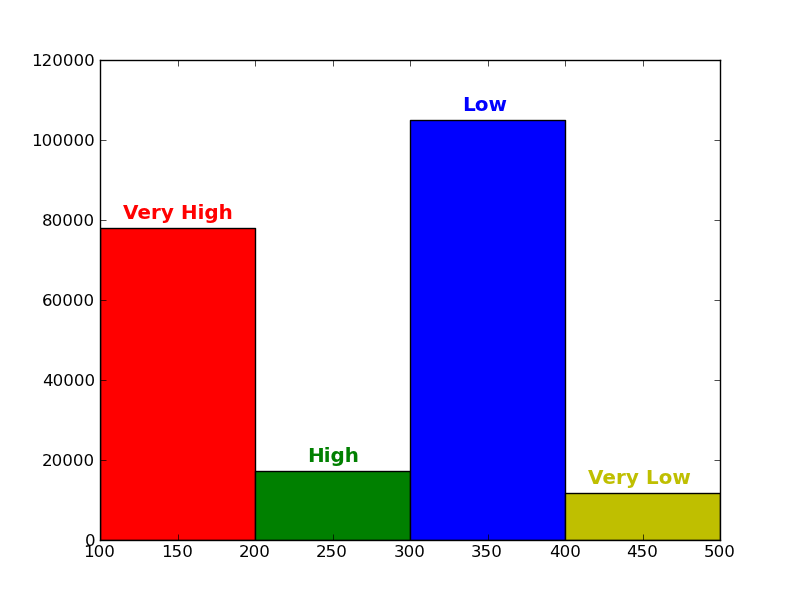
Current Statistics
Distribution of the Confidence of Uploaded Samples
How SARVAM Works
SARVAM uses a simple yet effective method for visualizing and classifying malware using image processing techniques. Malware binaries are visualized as gray-scale images, with the observation that for many malware families, the images belonging to the same family appear very similar in layout and texture.
Most of the new malware are modifications of existing malware. Thus the variants have almost the same content. For goodware, the newer versions usually have small additions/modifications to the previous versions. We maintain a database of more than 4 Million binaries comprising a blacklist of malware and a whitelist of goodware.
Users can upload new binaries and obtain the top matches using signal processing algorithms.
Example of similarity in Malware
The two images below represent gray-scale image maps of different Fakeran malware variants.
How long does it take to find a Match?
Computing Image based Similarity Feature: 50 ms
Finding Nearest Neighbor Matches with a 4 Million Malware Database on a single machine: 2 s (even faster matching time possible)
Some other peculiar Examples
Images of a spider and a girl visualised using the gray-scale images of some binaries
Related Publications
"Malware Images : Visualization and Automatic Classification". Lakshmanan Nataraj, S. Karthikeyan, Gregoire Jacob, B.S Manjunath - VizSec 2011
"A Comparative Assessment of Malware Classification using Binary Texture Analysis and Dynamic Analysis". Lakshmanan Nataraj, Vinod Yegneswaran, Phil Porras, Jian Zhang - AISec 2011